Proactive Cybersecurity: Safeguarding Edge Computing from Emerging Threats
As Edge AI adoption accelerates, cybersecurity threats are on the rise. At IEI, we take a proactive approach to securing our products against vulnerabilities. The IEI Product Security Incident Response Team (PSIRT) is dedicated to identifying, assessing, and mitigating security risks, ensuring that your edge deployments remain protected.
To further reinforce our cybersecurity commitment, IEI officially joined the FIRST (Forum of Incident Response and Security Teams) in 2024. As a globally recognized cybersecurity organization, FIRST connects IEI with leading security experts and incident response teams worldwide, enhancing our ability to share threat intelligence, adopt best practices, and respond to emerging threats effectively. This membership strengthens IEI’s cybersecurity framework, ensuring our customers benefit from more robust and resilient security measures.
Security Bulletins
Product Security Bulletins is listed below. Click on the click here link in the table to view more details.
Vulnerability Disclosure Policy
At IEI, security is our priority. We proactively integrate security into our products and work swiftly to address vulnerabilities. Through collaboration with customers, partners, and researchers, we ensure a safer computing environment.
Learn More >>How to Submit a Vulnerability Report
Reports can be submitted via 2 methods:
1. IEI Security Bounty program
The IEI Security Bounty Program is a collaboration between IEI and the research community. IEI believes that partnering with security researchers and promoting security research is essential to enhancing the security of IEI products. We encourage security researchers to collaborate with us in identifying, mitigating, and responsibly disclosing potential security vulnerabilities. We look forward to working with you! Refer to the IEI Security Bounty Program for more details.
2. Report Directly to IEI
We encourage developers and power users to report any potential or confirmed security vulnerabilities of IEI products to the Security Response Team. Please use the below PGP encryption public key to encrypt your email message, and send it to security@ieiworld.com
Security Incident Response Process
IEI currently utilizes the Common Vulnerability Scoring System (CVSS) version 3.x to assess security severity. The IEI Product Security Incident Response Team (PSIRT) serves as the central point for reporting potential security issues related to IEI products. IEI PSIRT collaborates with the broader security ecosystem, including security researchers, industry peers, customers, and vendors, to identify and address potential threats.
Working closely with various teams within IEI, the PSIRT team holds weekly meetings and follows a structured high-level process to ensure effective incident response and security management.
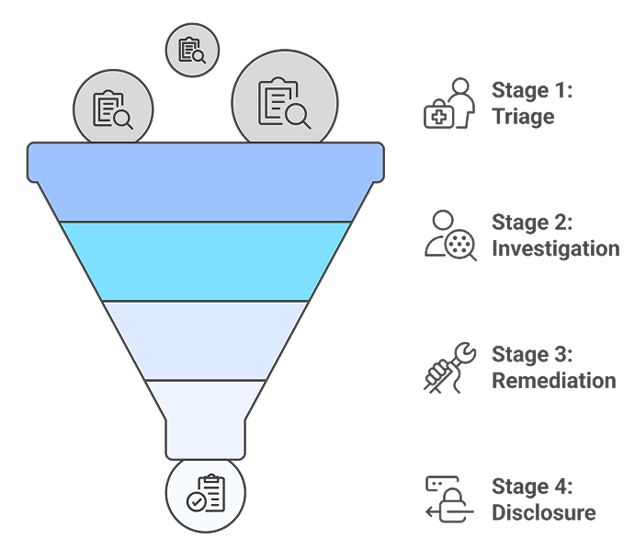
- Triage: Review the submitted information, validate the issues during the IEI PSIRT weekly meetings, assign a ticket ID, and identify the appropriate engineering team(s).
- Investigation and Analysis: IEI PSIRT collaborates closely with the product development team to pinpoint the root cause of the vulnerability and assess its severity and impact on IEI products.
- Remediation: If remediation is required, works with vendors and product development team to define approach and plans.
- Disclosure: Appropriate notification will be provided to affected customers and/or published in the Security Advisory section of our website regarding the product cybersecurity vulnerability.
Vulnerability Disclosure Policy
Our priority is to ensure timely security fixes and clear disclosure.
Read the policy →Security Bounty Program
IEI's Security Bounty Program rewards security researchers for reporting vulnerabilities in IEI software systems and IEI official website.
Learn More →

